No matter how you might take care of clients’ information, privateness legal guidelines require you to guard important data from prying eyes.
Nonetheless, that’s simpler stated than achieved with rising cybersecurity assaults and malicious actors. In line with Verizon’s 2023 Information Breach Investigation Report (DBIR), 83% of information breaches concerned exterior components.
In brief, it’s essential to shield your online business from exterior assaults.
Whereas there are a lot of methods to do this, your only option is to cease shady site visitors from getting into within the first place.
And in case you’re internet hosting your web site or software on a cloud, that’s what a cloud-based firewall is for.
Let’s see what a cloud-based firewall is, what it presents, and find out how to configure it correctly.
What Is a Cloud-Based mostly Firewall?
Cloud-based firewalls are software-based filters that enable or disallow the move of content material between your cloud infrastructure and the Web.
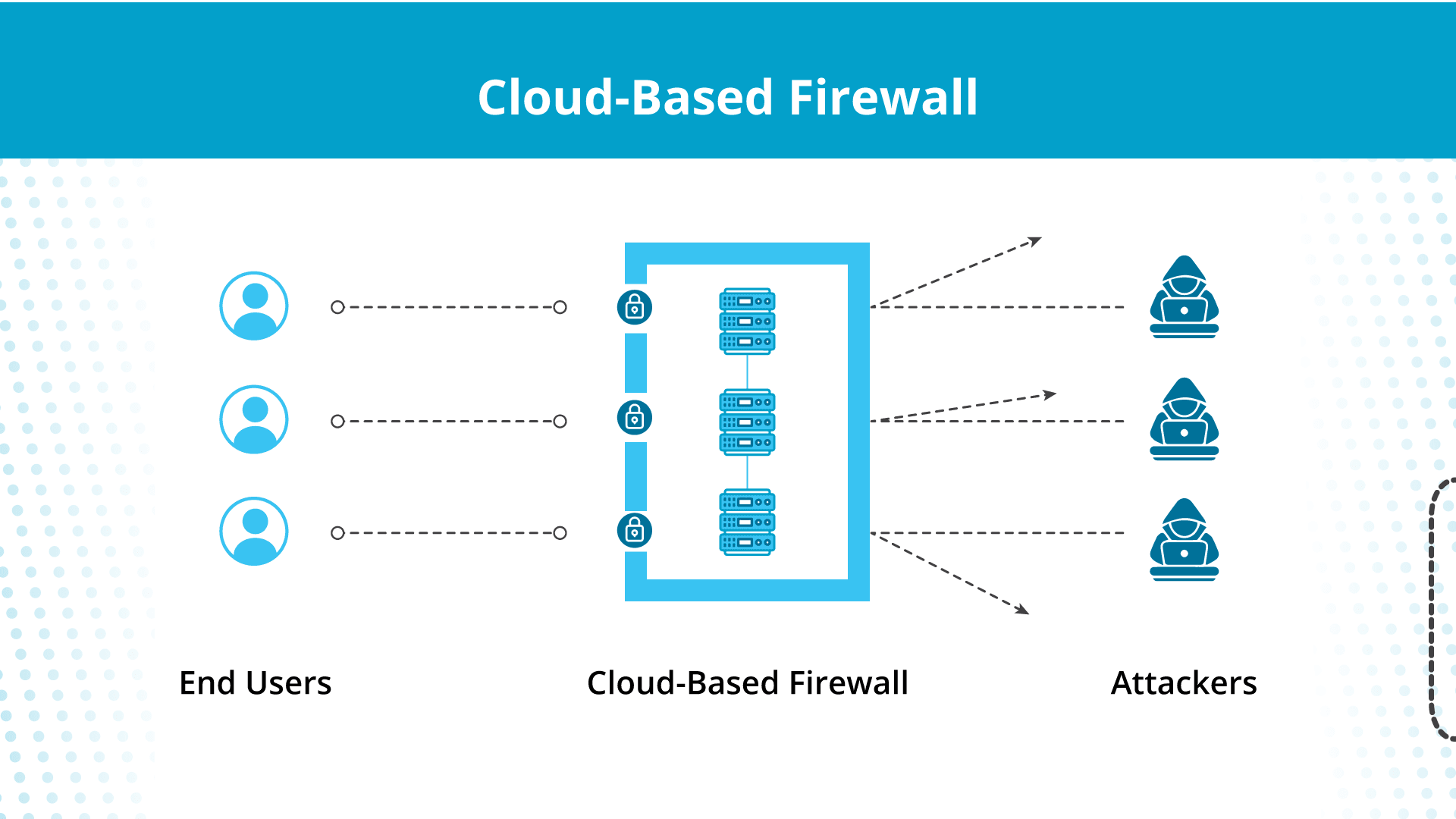
Consider cloud-based firewalls as safety guards who can differentiate between official clients and thieves based mostly on preset configurations. As an alternative of steel detectors to detect weapons, they use blocklists to limit site visitors with unfavourable signatures from getting into the cloud.
And, in contrast to conventional firewalls, cloud-based firewalls are based mostly within the cloud, in order that they shield your cloud content material no matter location.
How Do Cloud-Based mostly Firewalls Work?
Whereas a cloud-based firewall is situated on the cloud, it performs its capabilities like that of a {hardware} firewall.
- Site visitors monitoring — A cloud-based firewall separates the system from the Web, and all incoming site visitors has to go via its gates to enter your cloud.
- Filter-based entry — The firewall separates the great and dangerous content material based mostly on how the cloud supplier configures the filters. Licensed content material passes via, and unauthorized information stays outdoors.
- Restricted outbound site visitors — Moreover filtration of incoming site visitors, cloud-based firewalls prohibit outgoing site visitors so solely the permitted content material leaves your community. As an illustration, you wish to ship crucial API requests out however wouldn’t wish to ship delicate buyer information outdoors the community.
In brief, the fundamental working of the cloud-based firewall is equivalent to conventional firewalls. The variations seem solely once you have a look at the 2 sorts at a macro degree.
Cloud-Based mostly Firewalls vs Conventional Firewalls

So how do cloud-based firewalls evaluate with old-school bodily firewall safety guards? The reply sometimes is dependent upon your software.
In contrast to cloud-based firewalls that reside within the cloud, conventional firewalls are situated on the group’s on-premises server. As well as, whereas cloud-based firewalls are all the time a software program answer, conventional firewalls might include a software program answer or a bodily system.
{Hardware} specs restrict conventional {hardware} firewalls, and software program firewalls depend on on-premises computing assets. So if a site visitors spike happens on account of a distributed denial-of-service (DDoS) assault, they’ll’t scale as much as meet the useful resource demand.
In distinction, cloud-based firewalls have the flexibleness of the cloud and might scale up and down as required.
You’re additionally totally accountable for common upkeep and updates of the normal firewall. Upkeep of cloud-based firewalls, however, sometimes falls below the cloud supplier’s accountability.
Advantages of Cloud-Based mostly Firewalls
Whereas cloud-based firewalls are carried out for cloud safety, they provide a number of different extra advantages:
Scalability
Scalability and the cloud go collectively like espresso and mornings. In contrast to conventional firewalls, cloud-based firewalls can scale up and down based on want with out bandwidth limits.
Since cloud-based firewalls don’t rely upon on-premises bodily infrastructure, you’ll be able to shortly enhance the capability throughout peak site visitors calls for.
International Safety
Cloud-based firewalls are hosted on the cloud, so your community is protected globally no matter the place the incoming site visitors comes from.
With worldwide servers and edge content material supply networks (CDNs), you’ll be able to profit from this sturdy safety answer with out affecting the end-user expertise. The truth is, your customers will expertise decrease load instances and latency, relying on the place they’re situated.
Streamlined Administration
Whereas cloud-based firewalls allow you to create smaller software containers in your customers worldwide, you don’t must depend on their technical know-how to guard your community. As an alternative, you’ll be able to handle every thing from a central interface.
As an illustration, you should utilize the cloud-based firewall dashboard to:
- Replace safety insurance policies throughout all networks and places.
- View and monitor all safety occasions and potential threats.
- Apply safety patches to the entire cloud community.
Distant-Pleasant

Nonetheless, letting staff entry your safe system remotely means increasing your assault floor to malicious attackers. This is not excellent news in case you’re a HIPAA-compliant enterprise since you have to maintain delicate information protected from prying eyes.
Cloud-based firewalls resolve this distant work concern by letting you implement options like content material filtering and digital non-public connections to assist distant staff entry the system with out exposing it to the surface.
Automated Updates
Since 74% of information breaches contain human error, computerized updates are an ideal advantage of cloud-based firewalls.
In contrast to on-premises firewalls, the place your IT group has to use safety fixes and vulnerability updates manually, cloud-based firewalls obtain common, computerized updates straight from the cloud supplier.
Actual-Time Menace Intelligence
Cloud-based firewalls are powered by massive safety databases that assist them make data-driven choices in opposition to superior threats in actual time.
For instance, if a cloud-based firewall senses an assault sample on one aspect of the globe, it shares the knowledge with the remainder of the cloud infrastructure to enhance collective safety in opposition to rising threats.
Quick Deployment
Since a cloud-based firewall is software-based, you’ll be able to deploy it in virtually no time. That means that you can apply safety measures to your IT infrastructure in minutes as a substitute of ready for the {hardware} firewalls to be shipped and configured.
Sorts of Cloud-Based mostly Firewalls
Whereas each firewall on the cloud is a cloud-based firewall, there are completely different courses you have to think about to raised shield your infrastructure:
Public Cloud Firewalls
A public cloud firewall is a cloud-based firewall arrange by the general public cloud suppliers like Amazon Net Companies (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
A public cloud firewall sometimes creates safety safety across the digital machines and cloud storage and prevents unauthorized events from accessing your hosted content material.
When you have a point of flexibility, most public cloud firewalls work with predefined configurations to maintain the general cloud surroundings steady and safe and aren’t tailor-made to your particular wants.
SaaS Firewalls
A SaaS firewall, or firewall-as-a-service (FWaaS), is a cloud-based firewall. Organizations deploy these firewalls on their cloud infrastructure to filter transferring site visitors and determine threats inside it.
SaaS firewalls shield your IT infrastructure on a subscription foundation. As an alternative of manually configuring software-based firewalls on the VMs, you’ll be able to depend on the firewall supplier to deal with every thing.
Net Utility Firewalls
Net software firewalls (WAFs) are cloud-based firewalls designed for filtering and blocking web-based assaults on the software degree. They’re sometimes situated in entrance of net servers and apps since they assist filter HTTP and HTTP site visitors.
Web site internet hosting suppliers generally use WAFs as safety measures in opposition to SQL injections, cross-site scripting (XSS), and different widespread vulnerabilities of net functions like WordPress.
Subsequent-Era Firewalls
Subsequent-generation firewalls (NGFW) are sturdy firewalls that mix conventional firewall functionalities with a number of superior safety measures.

As an illustration, NGFWs provide:
- Intrusion prevention programs (IPS) — NGFWs monitor the community site visitors for identified assault signatures and patterns to forestall malicious brokers from reaching your delicate information.
- Deep packet inspection (DPI) — Subsequent-generation firewalls carry out deep packet inspections on the software layer to grasp the content material and context of the community site visitors. This lets NGFW implement a safety coverage based mostly on the content material of the information packets.
- Help for digital non-public networks (VPN) — Many NGFWs provide help for VPNs and assist you enable safe entry to distant staff with out the chance of information breaches.
How To Choose a Cloud-Based mostly Firewall
Whereas an NGFW might look like your finest guess for sturdy safety, it’s not all the time the optimum answer for each software. As an illustration, a WAF beats NGFW for widespread net functions by offering cost-effective safety with a simplified deployment.
Listed here are the highest concerns when selecting a cloud-based firewall in your software:
- Safety features — Make sure the firewall offers sturdy safety in opposition to related cybersecurity threats. As an illustration, in case you personal a SaaS software, search for DPI, application-aware filtering, menace intelligence, and DDoS safety.
- Efficiency — Consider how the firewall handles the site visitors. Guarantee it doesn’t have an effect on consumer expertise by rising latency or response time.
- Person interface — Assess if the firewall interface makes it simple to handle the entry management insurance policies and get real-time studies. If the dashboard is sophisticated, make sure the supplier presents documentation and buyer help to assist your IT group throughout onboarding.
- Compliance — In the event you should adjust to PCI-DSS or HIPAA, make sure the instruments and options wanted to safe delicate information per these safety requirements can be found.
- Redundancy and Failover — In the event you’re inclining towards a SaaS firewall, evaluate the firewall supplier’s failsafe mechanisms to make sure your infrastructure safety in case of accidents.
Finest Practices for Managing a Cloud-Based mostly Firewall
When you resolve on a cloud-based firewall, you may make it your individual by making use of customized safety guidelines and rules that fit your software. Nonetheless, you have to observe sure finest practices to make sure you profit from the firewall as a substitute of leaving the floodgates open for malware.
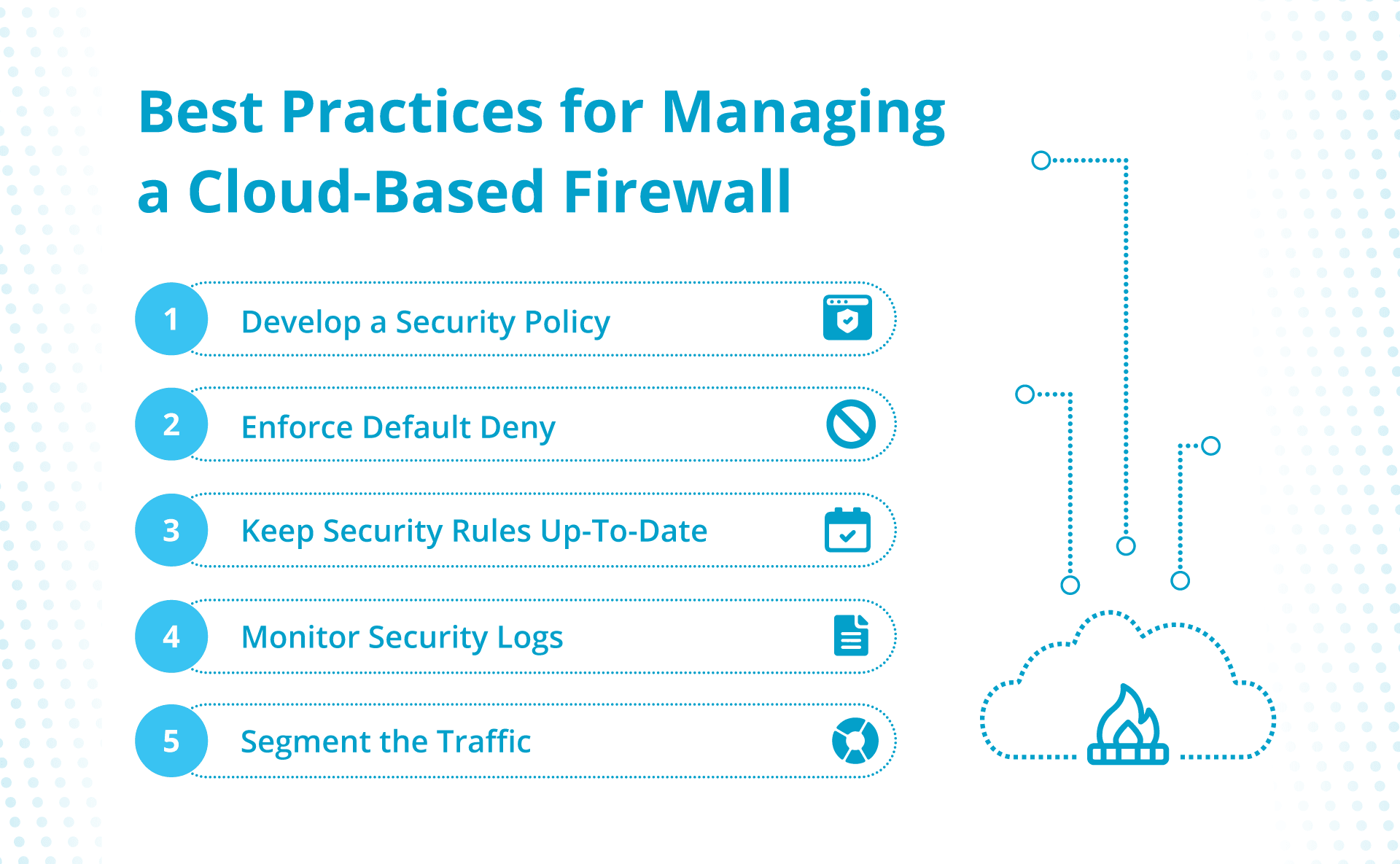
Develop a Safety Coverage
To begin off on the appropriate foot, set up a safety coverage for the cloud-based firewall that your IT group understands and agrees with. This fashion, everybody coping with the firewall will know what’s allowed and disallowed and might work collectively to watch potential threats.
For instance, think about itemizing supply channels for site visitors and the way a lot danger every carries. Take into account plugging that port if a selected channel brings meager site visitors however will increase safety dangers.
Implement Default Deny
Strategy configuration as if every thing is lava and there are a number of protected spots. In different phrases, as a substitute of blocking particular malicious site visitors, begin by blocking every thing after which solely permitting protected site visitors.
Maintain Safety Guidelines as much as Date
Since firewalls depend on preset configurations to separate protected and unsafe site visitors, maintain the safety guidelines updated.
Monitor Safety Logs
Allow logging to gather safety data of warnings and potential safety breaches. Overview them recurrently to guard your system in opposition to ongoing threats.
Phase the Site visitors
Phase the site visitors into completely different safety ranges and restrict entry to hosted content material based mostly on these ranges. This fashion, even when malicious brokers sneak via the bottom safety degree, they’ll’t contact the delicate data stream.
The truth is, this safety follow is required to adjust to lots of the information safety requirements. As an illustration, PCI-DSS requires you to create a buffer zone between the Web and cardholder information to solely enable the required site visitors to go via, which isn’t attainable and not using a firewall segmenting the incoming site visitors.
Ultimate Ideas: Cloud-Based mostly Firewalls — Boosting Cybersecurity With Ease
In the event you go for the appropriate firewall and handle it effectively, you’ll be able to higher shield your self in opposition to many of the widespread cyber threats that have an effect on fashionable companies.
Nonetheless, there’s extra to the safety equation than simply firewalls.
Our cloud devoted internet hosting options may help shield your community safety. Our ServerSecure Superior Safety comes with options like a standard firewall, malware scanning, vulnerability assessments, and DDoS mitigation.