The typical price of an information breach in 2023 was $4.45 million. That’s a 15% improve from 2020 and a regarding pattern for enterprises since they’ve intensive networks which are extremely focused.
That’s a part of the rationale enterprises are investing closely in community safety. A 2022 safety spending benchmark report reveals that firms in tech and enterprise providers spent 13% of their IT funds on cybersecurity.
Strengthening an enterprise’s community safety isn’t simple, nevertheless. There’s software program to observe, {hardware} to safe, prospects and distributors connecting by means of public networks, and staff to show and surveil.
This information covers all these components, together with sensible steps you possibly can take. First, let’s discover the importance of community safety, after which we’ll clarify enterprise community safety greatest practices.
In full, right here’s what you’ll be taught:
The advantages of enterprise community safety
Enterprise community safety refers to processes and insurance policies that improve the safety of information, accounts, endpoint units, and servers associated to an enterprise community.
Enterprises want tight safety as a result of a breach can result in delicate knowledge leaks, knowledge held for ransom, and the destruction of business-critical knowledge or applications. That’s not the one cause, although. Take into account the next motivations.
Compliance
Enterprises should adjust to knowledge safety rules relevant to their working areas. Community safety practices are undoubtedly essential to stop cyberattacks, which might expose delicate knowledge like prospects’ private and monetary info. This, in flip, exposes enterprises to authorized backlash.
Enterprise continuity
A hacker can maintain knowledge for ransom or convey down an enterprise’s community solely. This might jeopardize the corporate’s day-to-day operations. Cybersecurity is, subsequently, important to make sure the enterprise has a dependable uptime.
Shopper belief
Cyberattacks typically goal to compromise person knowledge, like passwords and personally identifiable info. Shoppers often lose belief in an organization that leaks their delicate knowledge. Consequently, this impacts the enterprise’s buyer retention and acquisition.
The main safety threats to enterprises
Enterprises with complicated networks typically face distinct safety threats. Maintain studying to get conversant in the vital ones.
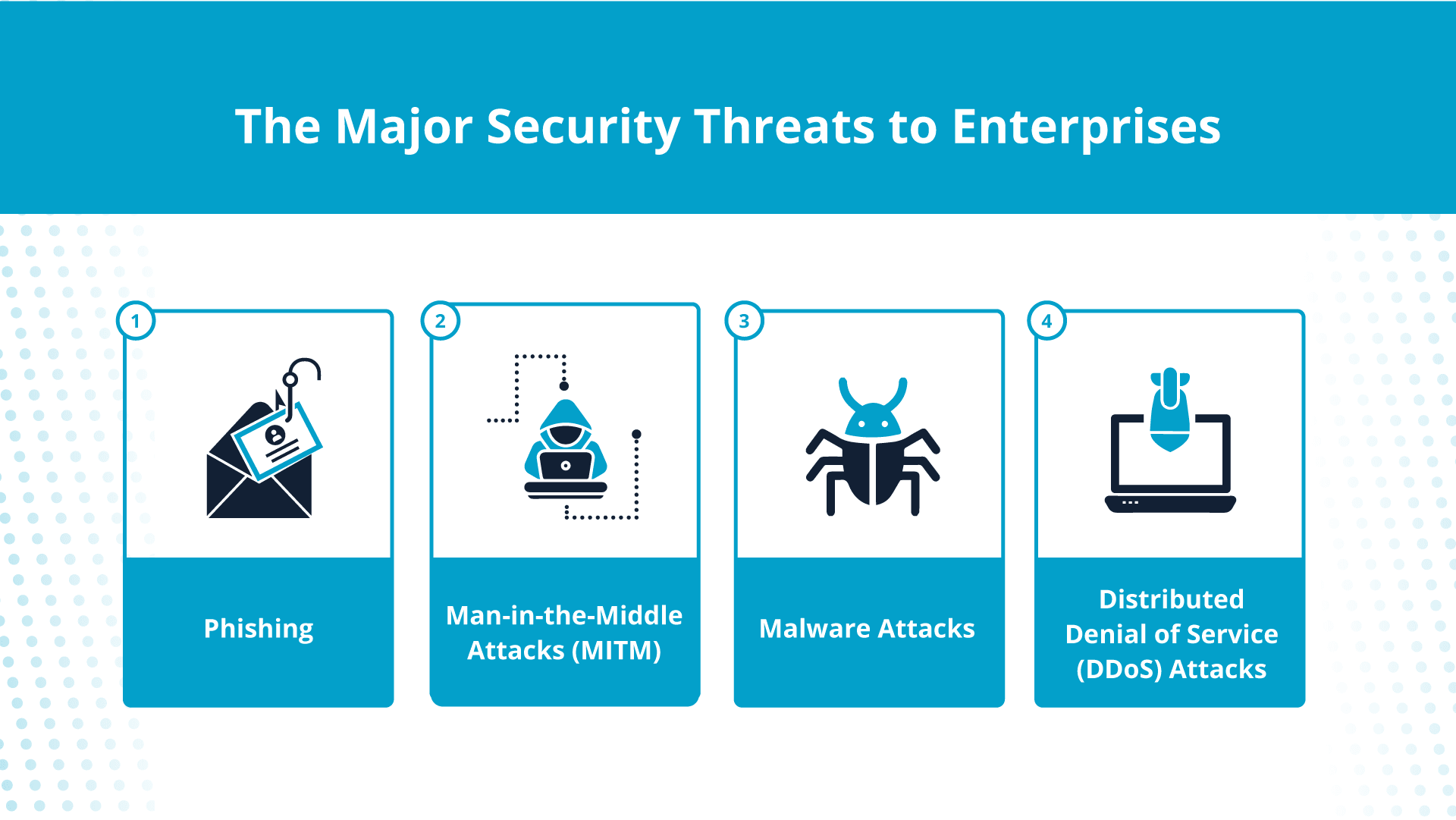
Phishing
Phishing includes an attacker sending somebody an e-mail or message disguised as official communication from a trusted sender. It’s a type of social engineering, which suggests the attacker manipulates or deceives the sufferer into compromising community safety by:
- Downloading malware.
- Clicking on malicious hyperlinks.
- Sharing delicate info.
Spam filters can filter out phishing emails to some extent. Nonetheless, refined phishing assaults are exhausting to detect by automated techniques and want educated people to establish them.
Man-in-the-middle (MITM) assaults
In an MITM assault, hackers hijack a server and shopper communication. They use packet sniffer or modifier instruments to intercept knowledge between the 2 endpoints.
Typically, MITM attackers goal to learn delicate knowledge or modify it to incorporate malicious content material. The attacker does this quietly with neither the shopper nor the server detecting a problem.
MITM assaults typically occur on account of vulnerabilities like a scarcity of Safe Sockets Layer (SSL) or Transport Layer Safety (TLS) protocols. For the strongest safety in opposition to MITM assaults, keep away from utilizing web sites that don’t adhere to HTTPS or SSL protocols.
Malware
Malware is malicious software program that may harm an enterprise community and extract confidential info. Listed here are a number of widespread kinds of malware:
- Ransomware: Locks the enterprise community and denies entry till the sufferer pays a ransom.
- Spy ware: Hides within the enterprise community, eavesdrops on communications, extracts knowledge, and sends it to the attacker.
- Trojan: Mimics official code till the hacker is able to launch a malicious assault.
- Worm: Replicates shortly and spreads by means of the enterprise community, overloading servers, consuming bandwidth, and slowing down operations.
Distributed denial of service (DDoS) assaults
In a DDoS assault, the attacker sends an enormous quantity of site visitors into community units like routers and servers. This flood of site visitors overloads the enterprise community, resulting in downtime and misplaced income whereas the servers are unavailable.
DDoS assaults will also be a strategy to camouflage a malware assault. The malware enters the community by means of the flood, undetected.
Considerably, there was a tenfold improve in DDOS assaults from 2005 to 2022, making it a prime precedence to deal with with greatest practices for enterprise community safety.
Insider threats
A community safety menace can originate from inside an enterprise. An worker or a third-party vendor may deliberately or unintentionally help in a malicious assault. A scarcity of community safety consciousness may play a job — however don’t rule out an intentional scheme.
You now perceive how a community safety breach can originate and have an effect on each an enterprise’s operations and repute.
Now, let’s discover some greatest practices that strengthen an enterprise’s community safety and skill to stop, detect, and reply to assaults.
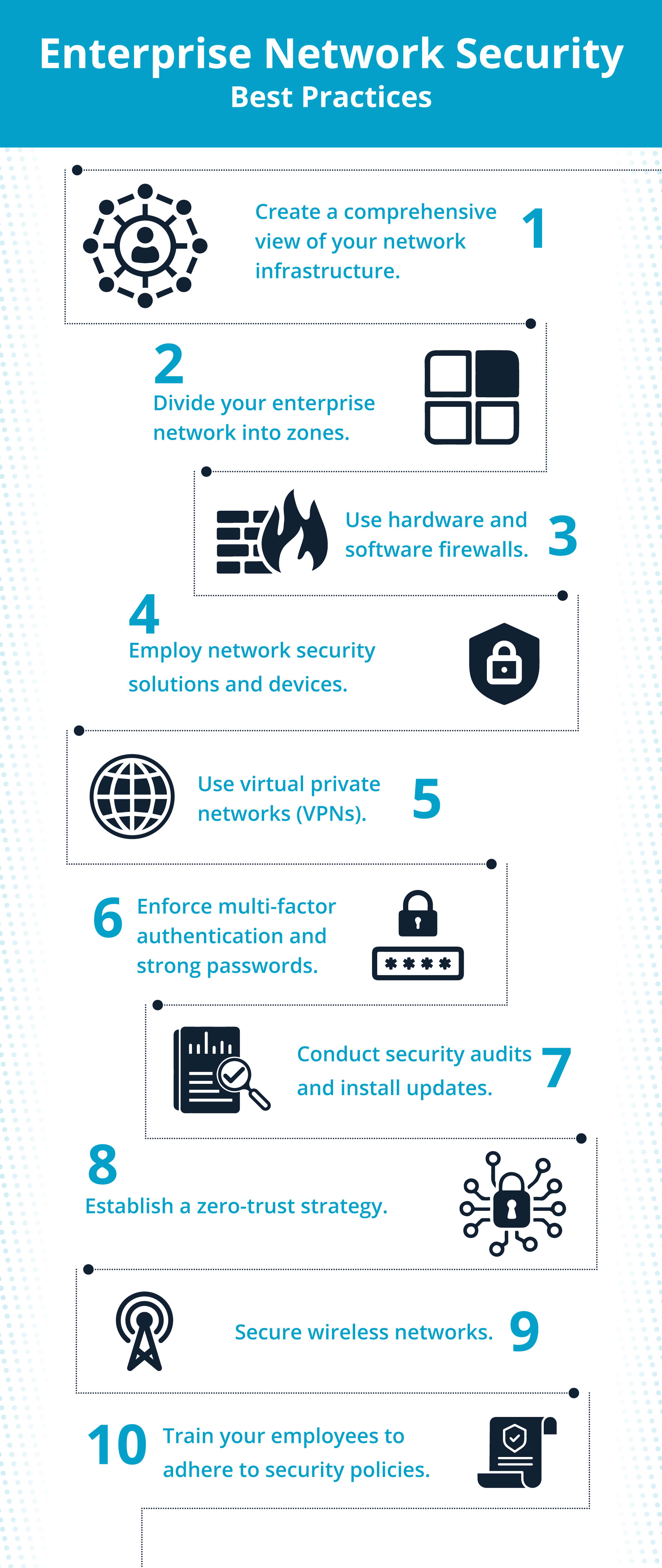
Enterprise community safety greatest practices
- Create a complete view of your community infrastructure.
- Divide your enterprise community into zones.
- Use each {hardware} and software program firewalls.
- Make use of community safety options.
- Safe wi-fi networks.
- Use digital personal networks (VPNs).
- Implement each multi-factor authentication (MFA) and powerful passwords.
- Set up a zero-trust technique.
- Prepare your staff to stick to safety insurance policies.
- Conduct safety audits and set up updates.
Take a better take a look at every of those community safety greatest practices.
1. Create a complete view of your community infrastructure
Enterprises typically have their knowledge and functions unfold throughout a number of servers, accessed by means of private and non-private networks. Due to this fact, step one in enterprise community safety is to realize a complete understanding of your community infrastructure.
Begin with the next parts:
- {Hardware}: Routers, hubs, switches, and firewalls.
- Software program: Intrusion prevention techniques and community entry management techniques.
- Endpoints: Desktops, laptops, and cell phones.
It’s a good suggestion to create a community diagram that reveals how community units and endpoints are interconnected. The depiction will put into perspective what number of native space networks (LANs), wi-fi networks, and vast space networks (WANs) are important to your enterprise.
When you have got a stable big-picture understanding, your decision-making improves.
2. Divide your enterprise community into zones
Divide an enormous enterprise community into logical zones. Every zone ought to segregate the community primarily based on the knowledge included and who wants entry. For instance, create separate zones for every division — or every native space, like flooring.
After segmentation, configure firewalls between zones. A firewall is a tool or software program that moderates site visitors out and in of a community.
Community segmentation makes a hacker’s work painstaking, as they have to assault every zone, and leaping from zone to zone isn’t straightforward. If a community zone is below assault, you possibly can disconnect it from different zones to isolate the menace.
3. Use each {hardware} and software program firewalls
Firewalls typically come as standalone community units you place between your enterprises’ community zones.
The firewall will analyze the information switch between these zones and prohibit malicious or delicate knowledge packets. Most routers and switches have built-in firewalls, so it is good apply to double-check they’re configured appropriately.
Whereas the enterprise firewall can forestall threats from outdoors, software program firewalls defend endpoints from any inner threats. Enterprise cybersecurity groups ought to implement software program firewalls on every community endpoint, like laptops, desktops, servers, and cellular units.
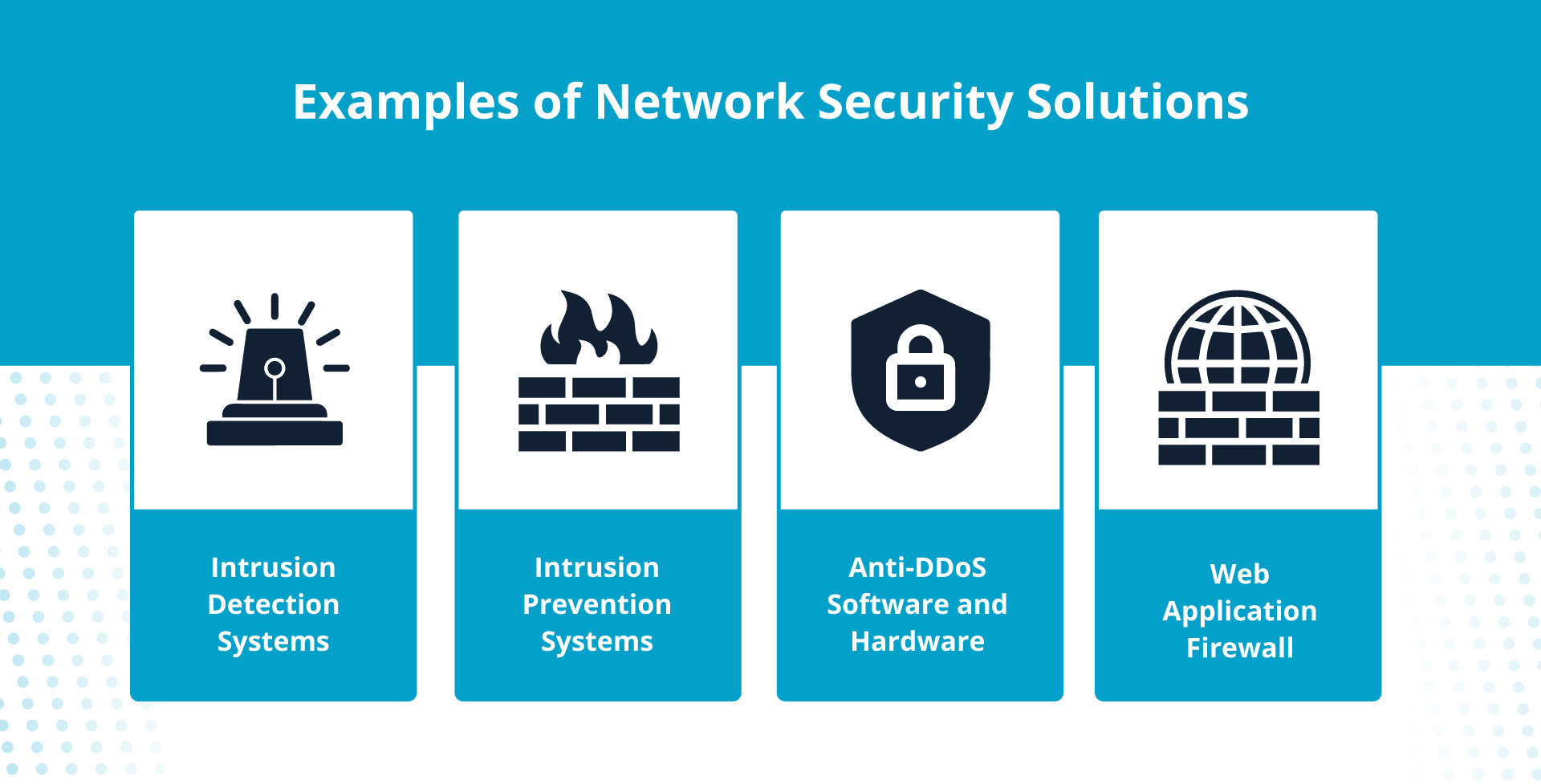
4. Make use of community safety options
Sure safety units and functions will assist thwart cyberattacks.
Intrusion detection and prevention techniques
An intrusion detection system (IDS) identifies malicious assaults in your community. An intrusion prevention system (IPS) is comparable, with the additional perform of stopping the assault.
An IDS will examine cyber actions with assault signatures — the attribute options of a cyberattack — and flag irregular on-line exercise like the next:
- Unauthorized file transfers.
- Adjustments in administrative privileges.
- Suspicious community velocity decreases.
However, an IPS is a machine studying system that automates menace detection and prevention.
Anti-DDoS software program and {hardware}
Anti-DDoS applications monitor your community site visitors, filter out suspicious knowledge packets, and block malicious server requests; this prevents volume-based cyberattacks whereas permitting official requests to succeed in your server.
Net software firewall (WAF)
Along with an enterprise firewall, use an internet software firewall to guard what you are promoting from assaults that focus on internet functions, akin to:
- SQL injection: Injecting malicious SQL code right into a database.
- Cross-site scripting: Injecting dangerous scripts right into a trusted web site.
- Cookie poisoning: Forging or manipulating a cookie to entry a person’s account.
A WAF will monitor the site visitors between your internet software and a shopper. It analyzes the information packets to filter out something suspicious.
5. Safe wi-fi networks
Wi-fi networks introduce extra safety challenges than wired networks. Wi-fi entry factors are susceptible to unauthorized entry, which leaves room for hackers to:
- Packet sniff to intercept unencrypted knowledge.
- Remotely entry your enterprise’s recordsdata.
- Mimic official entry factors to trick customers.
It’s a community safety greatest apply to safe your enterprise’s wi-fi community. Use wi-fi IDS and IPS techniques. Encrypt wi-fi knowledge utilizing Wi-Fi Protected Entry protocols, specifically WPA2 or WPA3.
Creating each a visitor WiFi community for guests and utilizing wi-fi isolation strategies to make enterprise info inaccessible from visitor wi-fi networks is significant.
6. Use digital personal networks (VPNs)
Many enterprises have a worldwide workforce that clocks in from their houses and different distant areas. The distant employees hook up with the enterprise community through the Web, a public community, consequently presenting a danger to enterprise community safety.
VPN software program solves this by creating an encrypted, personal connection between the distant pc and the enterprise community by means of the Web. Because the VPN offers a safe channel, the person can now safely use the general public Web to entry the enterprise community.
Mandate VPN utilization each time staff join remotely.
7. Implement each multi-factor authentication (MFA) and powerful passwords
Robust authentication strategies are a necessary a part of community safety.
MFA requires multiple authentication methodology earlier than granting entry to a community. The person has to validate their identification utilizing a mix of the next:
- Personally set passwords.
- Codes despatched to their e-mail or cellphone.
- Biometric validation, like facial scans.
- Bodily keys that plug into their machine.
If MFA isn’t sensible on your group, think about using different authentication strategies.
For instance, the energetic listing authentication methodology requires customers to supply their login credentials to an authenticating server (AS), which verifies the credentials and offers the person an authentication token that grants entry for a restricted time.
Regardless, what’s non-negotiable is insisting staff use robust passwords and alter them regularly.
8. Set up a zero-trust technique
An enterprise firewall protects the group’s inner community from outdoors threats, however inner threats may convey an enterprise community down.
The zero-trust technique is to authorize and authenticate each person, even when they join from a trusted machine on an inner community. ZTNA makes use of as many knowledge factors as potential to authenticate customers, akin to their credentials, areas, and machine well being.
A zero-trust technique offers customers the least potential entry wanted to finish their work. This entry is granted for a restricted time and ends as soon as the job concludes.
9. Prepare your staff to stick to safety insurance policies
Safety measures depend on staff and customers who comply with protocols and insurance policies. A 2023 report on the identification safety menace panorama revealed that 74% of individuals have been involved about knowledge loss on account of staff, ex-employees, and third-party distributors.
Therefore, coaching your staff to adapt to enterprise community safety practices is essential. Put money into coaching till staff at your enterprise know :
- Keep away from utilizing unsafe file switch strategies.
- Use each robust passwords and multi-factor authentication.
- Keep uptime on each firewalls and malware safety instruments.
- Detect and report phishing emails.
- Each use a VPN and follow safe web sites.
10. Conduct safety audits and set up updates
It’s not sufficient to configure safety units, instruments, and software program as soon as. Run a routine audit of your safety configurations, community units, and endpoints periodically.
Any new community machine wants double-checking for the right settings. Take a look at that your firewalls, VPNs, MFA, intrusion prevention software program, and all different safety units are working as supposed.
It’s additionally essential to replace your community units and endpoints. This contains the next:
- Updating each anti-virus and anti-malware software program.
- Putting in new safety patches and have updates.
- Changing community machine {hardware} with the newest model.
Now that you simply’ve discovered the perfect practices, right here’s a helpful guidelines you need to use to trace your progress.
Remaining ideas: Enterprise community safety greatest practices
Enterprise community safety is certainly a critical concern for giant organizations. Enterprise networks are prone to cyber threats — however now you understand how to implement greatest practices like community segmentation, multi-factor authentication, and zero-trust technique.
As soon as community safety greatest practices are in place at your enterprise, look ahead to full compliance with knowledge safety rules, clean and safe operations, and rising buyer belief.
The perfect internet hosting companion will make it easier to attain that objective faster. Get a head begin with Liquid Net’s enterprise internet hosting resolution; it markedly comes with DDoS safety, antivirus and malware scanning, vulnerability assessments, and intrusion detection techniques.