Enterprises more and more depend on cloud-based infrastructure to seamlessly ship functions, handle huge quantities of knowledge, and guarantee excessive availability. Plus, of people who use the cloud, a staggering 96% of companies use a public cloud both solely or as a part of a hybrid cloud answer.
Nonetheless, the widespread cloud migration from on-premises comes with new safety challenges, from the specter of malware and DDoS cyberattacks to inner knowledge breaches.
These threats demand sturdy safety options, together with safe and dependable cloud internet hosting.
For these contemplating migrating to the cloud or in search of new options to create a proactive safety posture, it’s important to grasp each the challenges and benefits of implementing a cloud-based safety answer.
Right here’s what we’ll cowl:
What’s enterprise cloud safety?
Enterprise cloud safety refers back to the applied sciences and insurance policies organizations make use of to guard their knowledge and infrastructure within the cloud. It applies to public, non-public, hybrid, and multi-cloud utilization.
Enterprises face threats, together with knowledge breaches, malware, and authorized ramifications ensuing from noncompliance with rules. As well as, id and entry administration is all the time a priority for firms with giant numbers of workers.
Enterprise cloud safety differs from client cloud safety in that it has a broader scale and scope, as giant firms cope with increased volumes of delicate knowledge that have to be processed safely – and sometimes in compliance with legal guidelines and strict trade rules.
Significance of safety in cloud computing
As enterprises more and more entrust important recordsdata, web sites, and functions to cloud computing environments – typically processing delicate and even labeled knowledge – it turns into extra vital than ever to prioritize safety.
The implications of even one incident may very well be catastrophic, with monetary losses and impacts to important providers like healthcare the place an assault might put sufferers’ lives in danger. A powerful 93% of enterprises report needing to be higher ready towards ransomware and different threats.
In a single examine, an alarming 80% of firms had skilled a cloud knowledge breach over an 18-month interval. Taking a proactive safety posture isn’t a precaution however an crucial.
Safety measures contain defending delicate knowledge, avoiding authorized entanglements related to regulation non-compliance, mitigating safety dangers via measures like zero belief, and conserving servers up to date and monitored.
Whereas dangers are there, utilizing cloud safety providers like automated backups can also be a key technique in catastrophe restoration that may reduce the affect of catastrophic occasions like excessive climate or widespread ransomware assaults.
How enterprise cloud safety works
The implementation of enterprise cloud safety covers a broad spectrum of methods, together with:
- Safe Enterprise Personal Cloud Internet hosting: Selecting a supplier that prioritizes safety is the inspiration of any cloud safety plan.
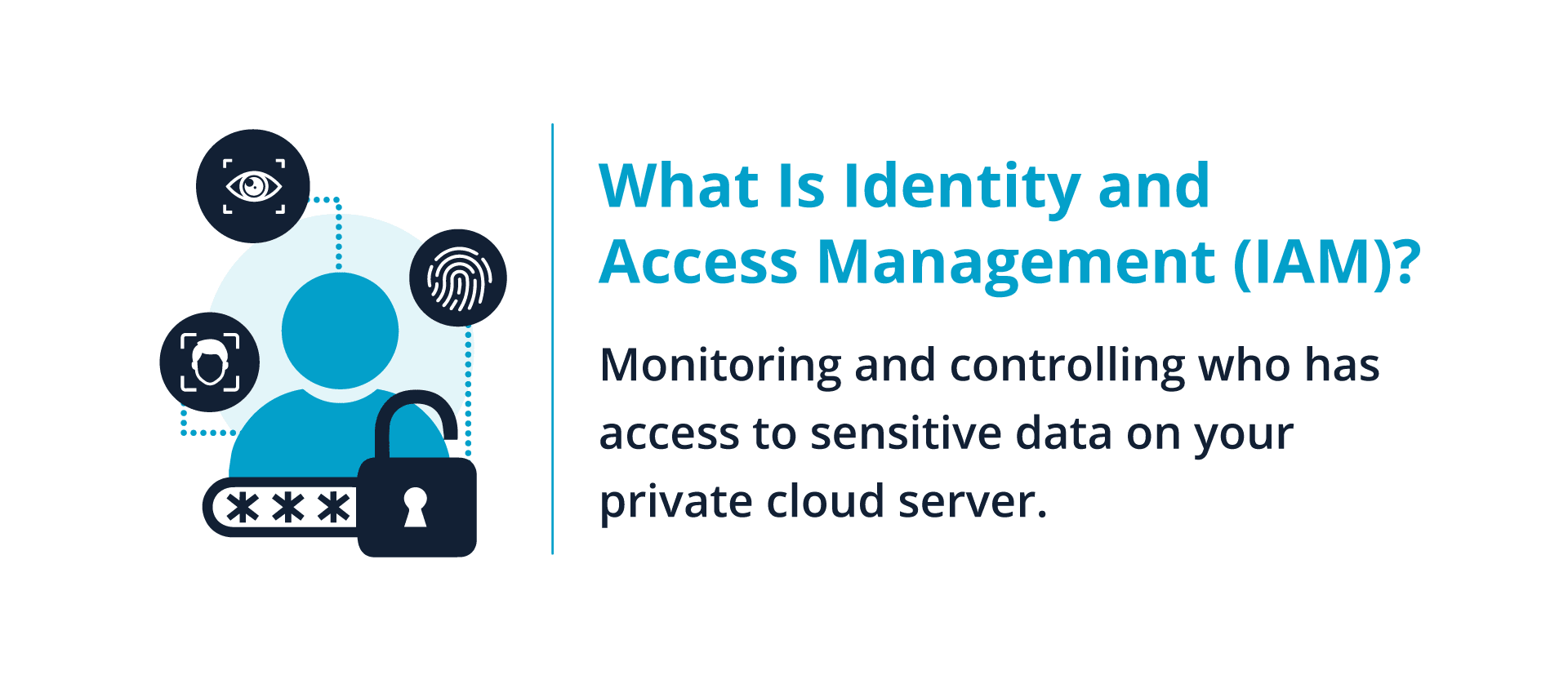
- Id and Entry Administration (IAM): Rigorous management over consumer identities and entry privileges helps mitigate unauthorized entry and knowledge breaches.
- Knowledge Encryption: Obfuscating delicate knowledge reduces the chance of use by unauthorized actors.
- Monitoring and Logging: Actual-time monitoring and logging will let you detect anomalies and potential safety breaches earlier than injury is finished.
- Knowledge Loss Prevention (DLP): Implementing DLP measures acts as a safeguard towards unintentional or malicious knowledge leakage.
- Regulatory Compliance: Enterprises in particular industries should stay compliant with authorized and trade rules like HIPAA or danger severe repercussions.
Menace Intelligence: This technique entails staying forward of cyber threats by analyzing the newest cybersecurity knowledge and proactively fortifying defenses.
Benefits of enterprise cloud safety

Since cybersecurity is in fixed flux as dangerous actors repeatedly discover new avenues of assault, and enterprise cloud safety providers provide a number of benefits to these seeking to sort out safety head-on.
Actual-time monitoring
Making an attempt to maintain observe of a number of VMs with inefficient monitoring instruments is problematic.
Cloud safety options present a centralized console the place you’ll be able to monitor threats and handle safety measures from a single interface, even when utilizing hybrid and multi-cloud setups.
Monitoring is real-time and fixed, alerting you to anomalies so your IT safety groups can reply to threats instantly or let automation care for the difficulty.
Fast deployment
In distinction to the time-consuming processes related to conventional safety fashions, safety on cloud providers will be deployed near-instantaneously. In important safety conditions the place seconds could make the distinction in stopping an assault or a system shutdown, the flexibility to make fast adjustments is important.
Cloud structure offers you scalability and agility that powers a fast response.
For instance, enterprise cloud environments can swiftly reply to threats like DDoS assaults and soak up the affect of malicious site visitors by quickly deploying further servers.
Deploying steady safety updates and patches can also be simpler on the cloud and will be performed with out interrupting operations. In conventional fashions, the deployment of patches may require important downtime.
Cloud options will let you swiftly and effectively allocate assets as you want them and improve your setup near-instantaneously – not like conventional safety fashions which will require intensive handbook changes.
Knowledge loss and knowledge breach prevention
Whether or not it’s delicate buyer data or commerce secrets and techniques, having your techniques breached and delicate knowledge being leaked or bought on the black market can destroy your popularity. And generally, huge swaths of knowledge are maliciously deleted, leaving you at a whole loss.
Enterprise cloud safety means that you can higher fortify your confidential data from potential breaches, stopping knowledge loss and breaches from impacting your online business. Plus, the inherent redundancy of cloud computing makes it a lot more durable to completely lose knowledge, particularly in case you have encrypted off-server backups like Acronis Cyber Backups with Liquid Internet.
Auditing and compliance reporting
Many industries like healthcare, finance, and authorities contracting require strict compliance with particular rules.
These will dictate the way you arrange components of your cloud surroundings and the way delicate knowledge is dealt with.
Even when you’re not a part of a extremely regulated trade, you could be affected by widespread compliance requirements just like the Basic Knowledge Safety Regulation (GDPR) and The California Shopper Privateness Act (CCPA).
Personal cloud options provide instruments to observe and audit your environments, making certain they continue to be compliant with rules to keep away from hefty authorized charges or different penalties.
Challenges of enterprise cloud safety

Enterprises face a wide range of threats that make them implement cloud safety. Insufficient safety providers and instruments might result in devastating monetary losses.
Cyberattacks
With their wealth of delicate data, enterprises should cope with a relentless assault of tried cyber crimes starting from malware to ransomware to DDoS assaults.
Plus, 73% of organizations in 2022 confronted ransomware assaults that might embrace wide-scale deletion of important knowledge. With out separate failsafe backup techniques, failing to pay up in time ends in knowledge deletion and generally widespread system corruption.
Whereas inner dangerous actors exist, most breaches contain exterior actors, and 74% contain a human component. That human component typically makes use of social engineering or just takes benefit of human error by your workers to entry your community.
Automated assaults aren’t the primary safety danger; it’s your workers making errors.
Insufficient Id and Entry Administration (IAM) giving the unsuitable folks entry to delicate knowledge, unencrypted recordsdata being intercepted, or poorly secured non-public cloud internet hosting leaving exploits open amplify human errors.
Non-compliance
Nearly all industries may have some degree of compliance they need to adhere to.
For some companies, it’s so simple as following client privateness guidelines. Others, just like the healthcare trade, are sure by stricter authorities rules, reminiscent of HIPAA guidelines round dealing with confidential affected person knowledge.
Failing to fulfill these rules has direct penalties past simply being learn the proverbial riot act and getting a slap on the wrist. These can embrace hefty fines or jail time for these accountable in some circumstances.
Compliance with some requirements, just like the Fee Card Business Knowledge Safety Customary (PCI DSS), isn’t all the time a federal legislation. Nonetheless, failing to observe these trade tips nonetheless has severe penalties, reminiscent of not with the ability to settle for bank cards as a fee technique.
In addition to that, deliberately failing to stay compliant might severely injury your popularity, particularly if the neglect ends in a buyer or consumer knowledge breach.
Nonetheless, high-quality non-public cloud hosts like Liquid Internet have many compliance requirements in-built as a part of their cloud-native processes, so establishing a compliant surroundings is way simpler.
Insufficient safety measures
Whereas your group is in the end answerable for its safety hygiene, a safe cloud host like Liquid Internet with sturdy safety providers types the sturdy partitions defending this basis from exterior threats.
Encryption protocols, entry controls with acceptable permission administration like zero belief measures, and proactive monitoring towards rising threats are a few of what your cloud host can assist with. Selecting one which falls flat or doesn’t align together with your group’s safety posture is a positive step towards catastrophe.
Enterprise cloud safety finest practices

Sticking to cloud safety finest practices is crucial when managing your organization’s cloud migration.
Perceive the shared duty mannequin
In brief, each your group and your cloud supplier share safety tasks. Whereas the supplier secures the cloud infrastructure and a few APIs, your group is answerable for safeguarding knowledge, functions, and consumer entry.
These boundaries be sure that cloud suppliers should not blamed for points exterior their management, and your online business isn’t accountable for points arising from vulnerabilities within the underlying infrastructure.
Shield consumer knowledge and knowledge
Implementing Id and Entry Administration (IAM) is essential. Controlling consumer entry and logging all consumer exercise are the primary steps to conserving unauthorized customers away from labeled data.
Encrypting knowledge offers one other layer of safety when dealing with delicate knowledge and needs to be performed at relaxation and in transit.
Preserve techniques updated
Whereas that is probably the most elementary rule in all of cybersecurity, many enterprises wrestle to observe it. Implementing patches will be an ordeal in huge enterprise-level digital environments, however it’s nonetheless needed.
At all times hold your software program and firmware updated with the newest patches. This alone might forestall malware, ransomware, and different exploits from ever reaching your servers. Hosts like Liquid Internet usually robotically replace firmware and different IT infrastructure gadgets.
Implement safety monitoring
Implement a complete community safety monitoring technique to detect and reply to potential threats promptly.
This will contain reviewing logs repeatedly, establishing automated alerts for suspicious exercise, and making a plan for a way your crew escalates and offers with threats of varied ranges.
Make the most of cloud-native safety providers
Select a cloud supplier with instruments and providers like cloud-native firewalls that may study from risk patterns and reply to rising new malware strains.
Develop an enterprise safety technique
It’s essential to be ready for any risk. A safety technique will be the distinction between dropping thousands and thousands of {dollars} per minute when servers are down or mitigating and quarantining an assault.
When growing your technique, ask questions like:
- How will you practice your crew to cope with safety threats?
- What instructional supplies might you create to assist them?
- Might you elaborate in your knowledge insurance policies that govern the dealing with of delicate data?
- What about compliance auditing insurance policies?
Your technique must also embrace implementing an incident response plan so all workers know what to do in case of an assault. The quicker you cope with a breach, the faster you reduce the injury.
This enterprise cloud safety guidelines will assist get you began in figuring out the subsequent steps to take.
- Doc your group’s tasks underneath the Shared Accountability Mannequin.
- Set up stringent safety controls and implement Id and Entry Administration (IAM) practices.
- Encrypt delicate data and arrange multi-factor authentication (MFA).
- Repeatedly again up important knowledge.
- Repeatedly apply safety updates to software program and firmware, together with software-as-a-service (SaaS), platform-as-a-service (PaaS), and infrastructure-as-a-service (IaaS) apps and packages.
- Develop a plan for monitoring and auditing cloud actions.
- Evaluation logs repeatedly.
- Arrange alerts for suspicious actions and create a set of safety insurance policies.
- Use cloud firewalls that proactively study and reply to new threats.
- Outline and doc knowledge insurance policies.
- Set up auditing protocols.
- Create instructional supplies for worker coaching.
- Implement an incident response plan for swift and efficient responses to safety breaches.
Learn how to choose the appropriate cloud safety answer
Whether or not your organization makes use of public or non-public cloud or a mixture with hybrid cloud or multi-cloud options, you want a robust enterprise cloud safety companion. When choosing a cloud safety providers supplier, contemplate the next:
Assess your online business wants
Begin by evaluating your particular enterprise necessities, together with needed compliance requirements, safety necessities, managed/unmanaged entry, workloads, cloud assets wanted, and scalability expectations.
Evaluate safety features
Every host will provide a unique degree of safety. Search for encryption protocols, firewalls, automated backups, DDoS safety, and extra safety measures. With Liquid Internet’s VMware Personal Cloud, you profit from a devoted firewall, DDoS safety, common Acronis backups, and single-tenant isolation to make sure the security of your important workloads and knowledge.
Consider efficiency and scalability
How a lot do you anticipate your enterprise’s cloud wants to vary? Search for a scalable host that may develop with you and may deal with elevated workloads. Additionally, search for a high-performance community and storage choices. Liquid Internet affords extremely out there infrastructure constructed on redundant enterprise-grade {hardware}.
Search for strong administration and assist
Good administration takes the issue out of dealing with an enormous VMware surroundings. Liquid Internet displays and manages your total digital knowledge heart, permitting you to focus in your functions while not having specialised VMware data. Plus, 24/7/365 assist is offered from the Most Useful People in Internet hosting®.
Contemplate price and pricing fashions
Search for clear pricing (fixed-rate or pay-as-you-go) and the cost-effectiveness of every answer. Liquid Internet’s pricing ensures you solely pay for what you employ and may improve anytime. Plus, there are not any per-VM charges.
Assess infrastructure compatibility
Interact with potential cloud hosts to grasp how effectively they will accommodate your present infrastructure. Many enterprise hosts provide a free session. For instance, you’ll be able to take the one-on-one 7-Level Infrastructure Evaluation earlier than buying Liquid Internet’s VMware internet hosting.
VMware Personal Cloud meets and exceeds the wants of most enterprise purchasers and affords assist with the Most Useful People in Internet hosting®.
Remaining ideas: An entire information to enterprise cloud safety
Enterprises on the cloud face a wide range of challenges and threats, however a strong and dependable non-public cloud answer can reduce these points whereas additionally growing efficiency and managing prices.
Implementing sturdy safety practices with a bunch that provides managed internet hosting helps share the load and improve safety.
VMware Personal Cloud by Liquid Internet affords top-notch safety features, clear pricing, scalability, and reliability to make sure your companies can seamlessly transition to a safe virtualized surroundings and proceed to develop.